When you get a minute, take a look at the OS/400 Create default public authority system security value, QCRTAUT, and the default parameters on your OS/400 library definitions. QCRTAUT is a system value I found on my OS/400 V4R4 and V4R5 machines
that—along with library descriptions—plays a critical role in what default authorities the *PUBLIC user automatically receives whenever a new system object, such as program or a library, is created. What I found surprised me because QCRTAUT is a fairly universal value that isn’t written up too much in the OS/400 press but its application can have a significant effect on your OS/400 security.
Who Is *PUBLIC and Why Should I Care?
*PUBLIC is OS/400 shorthand for those users who are accessing an object for which there is no specific authority explicitly granted. *PUBLIC is a fail-safe for when an OS/400 resource is requested and the operating system doesn’t have any clear instructions for what kind of authority to provide for that user. OS/400 provides *PUBLIC authority to an object for users meeting all these specific criteria:
• They don’t having specific authority to the object.
• They are not on an authorization list for the object.
• They are in a group profile with no specific authority to the object.
It is a catchall category that tells the system what to do when you haven’t provided explicit instructions for what a particular user can do with a particular object. It’s also important because—as AS/400 and iSeries boxes migrate out to the Internet—locking down *PUBLIC security becomes a bigger issue than it was when machines only ran on a private internal network. Okay, so if *PUBLIC is default authority for an object, where does it get its default values for a newly created object? (Hint: Think QCRTAUT and your OS/400 library descriptions.)
Figuring It Out
To answer that question, I created a new library on my V4R4 AS/400 called HERTVIK1 by using the Create Library (CRTLIB) command with the default parameters:
CRTLIB LIB(HERTVIK1) TYPE(*TEST) TEXT(‘Joe test library’)
Then, I ran an Edit Object Authority (EDTOBJAUT) command as follows to see what kind of default authorities OS/400 created for access to HERTVIK1.
EDTOBJAUT OBJ(HERTVIK1) OBJTYPE(*LIB)
I received the screen shown in Figure 1. As you can see, the Object authority for user *PUBLIC is automatically set to *CHANGE for library HERTVIK1. This means that any OS/400 user can go to the HERTVIK1 library and be able to change, delete, or modify data files in this library (unless this setting is overridden by another set of controls for an object). This is not a good situation for default data authority for an unidentified user.
To test this fact, I entered a simple OS/400 Create Physical File (CRTPF) command to create an 80-character file called ORDERS in library HERTVIK1 and—when I performed a EDTOBJAUT on that file—the *PUBLIC authority on HERTVIK1/ORDERS was also set at *CHANGE. Again, this is not a great situation because undefined users could add, delete, and change records at will, and I did this as a test user with the good old DFU utility. However, *CHANGE will prevent the creation, clearing, and deletion of files for *PUBLIC, so that protection mechanism is in effect. At this point, I knew that my AS/400 was automatically setting *PUBLIC access to these libraries and files to *CHANGE but I didn’t know how.
So How Did My Library Get This Way?
As you might imagine, I was curious about this so I dug in, deleted the library, and recreated it again with the CRTLIB command. This time, however, I prompted the command to look at all of the parameters I could set and the prompted command gave me the display shown in Figure 2.
Looking under the additional parameters for the CRTLIB command, I found two parameters that have a great deal to do with what authority *PUBLIC users have to the library itself and what authority *PUBLIC users will have to newly created objects residing in that library. Here’s what these parameters do and why you should be concerned about them:
• Authority (AUT)—Defines what authority *PUBLIC users have to the library itself. The default value, *LIBCRTAUT, specifies that the new library will have the same authority as its parent library, the QSYS library. In my case, QSYS was set to provide *USE authority for *PUBLIC, which is probably why unknown users are unable to create, delete, clear, or modify objects in the HERTVIK1 library.
• Create authority (CRTAUT)—Specifies the authority given to *PUBLIC users to an object created in this library. The default, *SYSVAL, specifies that objects in this library will be given the same data authority as that listed in the Create default public authority system value, QCRTAUT. As a result, this system value controls what *PUBLIC users can do with objects that are created in their library. This value can be overwritten to another setting (e.g., *USE or *EXCLUDE) but its default value is *CHANGE.
Between these two default parameters, OS/400 decides what *PUBLIC can and cannot do in a specific library. For data authorities (remember I was able to create, change,
and delete records as a *PUBLIC user), the QCRTAUT system value on my system is set to *CHANGE, which is its shipping value. If you want to check out QCRTAUT, you can change and modify it by using the Work with System Values (WRKSYSVAL) command on the green-screen, or you can change it in AS/400 Operations Navigator (OpsNav) by following the Security>Policies> Security Policies nodes (it’s included under the Security Controls tab of the Security Policy Properties screen that shows up when you follow this path).
Not Just for CRTLIB and Be Careful
Once I understood how OS/400 targets these values, I started finding Authority (AUT) or Create authority (CRTAUT) parameters in many common OS/400 statements. What I found is that—in most of the OS/400 CRTxxxxxx commands I opened (such as CRTPGM, CRTPF, CRTRPGPCM, CRTCLPGM, etc.)—there is generally an AUT parameter in each of these commands and its default value is set to *LIBCRTAUT. *LIBCRTAUT means that the default authority for the new object is dependent on whatever was specified in the Create authority (CRTAUT) parameter of the library in which the object is being created. If you don’t change the QCRTAUT system value or the CRTAUT parameter when you’re creating a library, in most cases the default *PUBLIC authority for your OS/400 objects will be whatever is contained in the QCRTAUT system value (which, again, is shipped with a default value of *CHANGE).
To change these default *PUBLIC creation authorities, you have several options:
• You can change the QCRTAUT system value to *USE or *EXCLUDE or another setting depending on your security plan. Be aware, however, that QCRTAUT is also used in a number of other commands, such as Create Device Description Display (CRTDEVDSP), and in the OS/400 automatic configuration utility, AUTOCONFIG, that creates new devices when an unknown terminal signs in on your network. If you change QCRTAUT to a more restrictive value (e.g., *USE or *EXCLUDE), that change may impact other areas of your system where a default assignment of *PUBLIC authorities is also dependent on QCRTAUT.
• You can change the default *PUBLIC authorities for a library by explicitly defining them when you execute the CRTLIB command. I recommend that you look at the default values for *PUBLIC authority when you create a library and select the values that fit into your security scheme. Think about your *PUBLIC authority scheme and don’t automatically take the defaults on library creation because these defaults will trickle down to newly created objects in your library.
• You can change library-specific default *PUBLIC authorities by using the Change Library (CHGLIB) command. If you select the F10 (Additional Parameters) key on CHGLIB, you will see an option to change the Create authority parameter for that library. If you enter *USE or *EXCLUDE there, this new option will take effect for any new objects that are created in your library.
• Individual file authority changes can be implemented by using the EDTOBJAUT command. If you need to change the Object authority, you can use this command to review your objects and remove the *PUBLIC *CHANGE authority.
As you can see, OS/400 has a fairly comprehensive method for assigning *PUBLIC authorities to objects. Once you understand this method, you can manipulate it in your favor to save work and make your system more secure on your network and on the Internet.
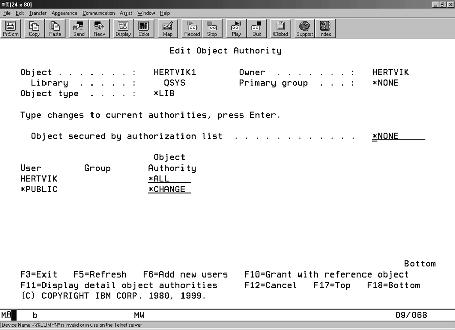
Figure 1: Here are the default *PUBLIC authorities that OS/400 assigned to my library when I used the CRTLIB command.
Figure 2: If you prompt the CRTLIB command, you’ll soon understand how OS/400 arrives at the *PUBLIC authority settings that it uses.












 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online