The System i operating system comes with a couple of commands that allow you to see the contents of the audit journal. The Display Audit Journal Entry (DSPAUDJRNE) command copies the entries to a display or report. However, the command has not been updated for a few years, and it misses some of the newer entry types and formats. The Display Journal (DSPJRN) command can dump any journal receiver to an outfile (database file). In both cases, the result is an unformatted file that you can massage using your favorite query tool, such as SEQUEL.
The problem with both of these approaches is that they do not include other sources on the system that track a job or user and their associated entries to create a complete audit trail. To fully investigate a security event, you might also need to look for information in QSYSOPR and QHST. In addition, the exit point history for critical servers—such as FTP, ODBC, JDBC, and so on—can provide valuable information. If you have all of these sources, you can more accurately piece together the trail for a job or user on the system.
Robot/SECURITY Uncovers the Transactions
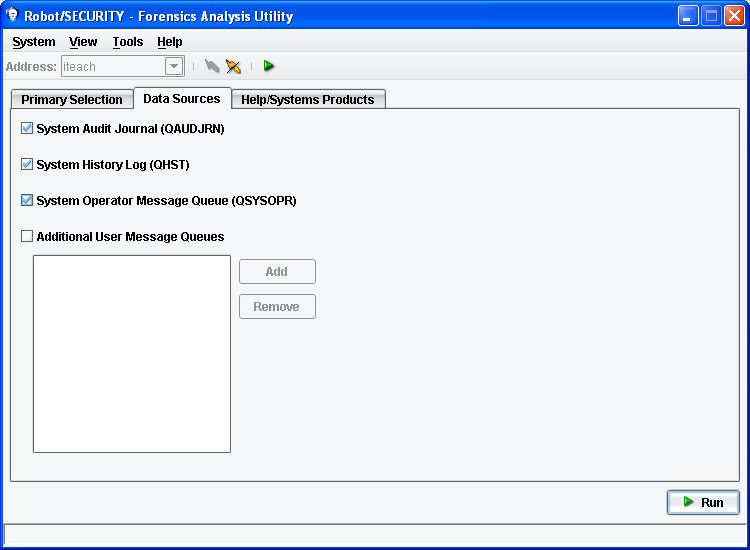
Robot/SECURITY can take the security-related events for a date range, job, or user from multiple sources on the system and build exactly the output you desire. You can select from a list of potential system sources, such as QAUDJRN, QHST, and QSYSOPR (see Figure 1). In addition, the Robot/SECURITY database contains usage data for the common communication server exit points. It also maintains detailed log entries for user actions during profile exchange operations. You select the sources of information to include. The result is that your auditor gets a clear picture of what was accessed on the system.
Figure 1: You can select from multiple sources of security-related events on your system. (Click images to enlarge.)
From Security Sources to the Detail
When you click Run, Robot/SECURITY interrogates your system to obtain the detailed entries. After all sources are checked, it displays the information in a graphical display directly on your PC. The entries are summarized by source type and include a counter of the number of entries from each source (see Figure 2). QAUDJRN is further broken down by entry type for each audited area, such as PW (Password Failure) or AF (Authority Failure). Robot/SECURITY's Forensics Analysis Utility also offers a data filter that allows you to limit the data shown to the entries that meet the criteria you specify; for example, you can display only entries related to a specific file or library.
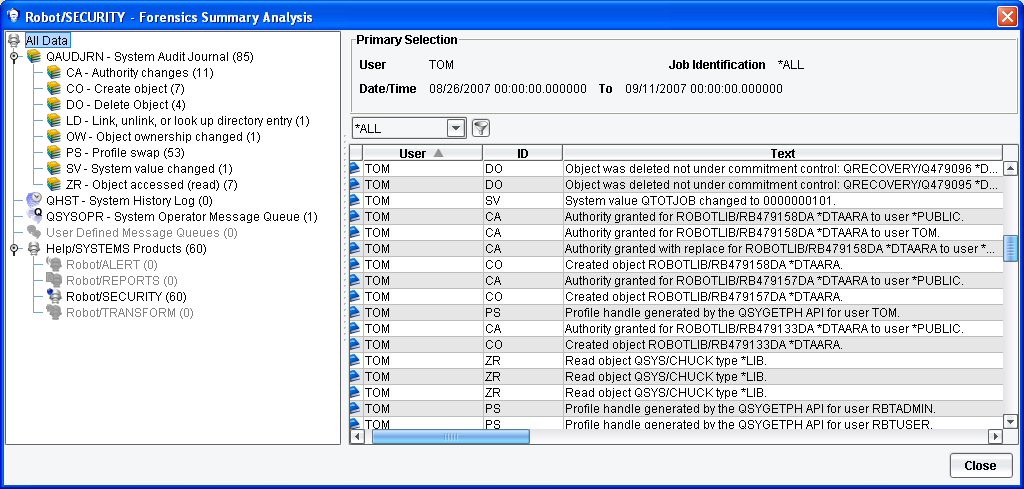
Figure 2: Robot/SECURITY shows the detail transactions for a user over a specified time period.
Robot/SECURITY is really five security products in one package; Forensics is just one part of the product. Give it a trial to see the other components, which include exit point monitoring, QAUDJRN monitoring, security auditing, and profile exchange. Call 800.328.1000 to request a demo or a FREE 30-day trial. And check out Help/Systems' other offerings in the MC Showcase Buyer's Guide.












 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online