Get started with PCI and learn why every company should be in compliance.
Few things strike fear into the hearts of consumers and businesses more than a breach of financial information. Why? Because it hits us where we're most sensitive: our pocketbooks! Long gone are the "good ol' days" when hackers were motivated by the challenge of breaking though security. While arguably no less troubling, a guarded admiration and respect was earned as a result of the intelligence and creativity exhibited by those early individuals. After all, these cyber-battles often pitted the little guy against "the Man." The more impenetrable the defenses, the greater the respect garnered by the individual who was able to break in.
While modern underground hacktivist groups like Anonymous still claim to access—and publicly expose—information on practices they feel contravene the public's best interests, modern hackers often seek far more basic information, such as consumer email addresses, Social Security numbers, and passwords. This information is subsequently used to gain access to Web sites or to facilitate social engineering attacks.
Nowadays, financial gain is often the primary motivation. The majority of the world's business transactions are conducted electronically, opening up new opportunities for criminals. It didn't take long for organized crime to realize that vast amounts of money could be made using and abusing the technology we all rely on. The borderless nature of the Internet means that computer crimes are not restricted to a neighborhood, region, or even country. Compromised data is often resold many times, commencing only a matter of moments after it has been obtained.
Many credit card issuers protect customers with "zero liability" for fraudulent transactions; however, any breach or abuse impacts us all, regardless of how the data was obtained or used. In 2006, in response to the explosion of credit card–related crimes, five major issuers (MasterCard, Visa, American Express, Discover, and JCB International—known collectively as the Payment Card Industry, or PCI)—formed the Security Standards Council (SSC). The SSC designed a framework of six categories with twelve primary requirements, and a comprehensive assessment and penalty process as represented in the table below.
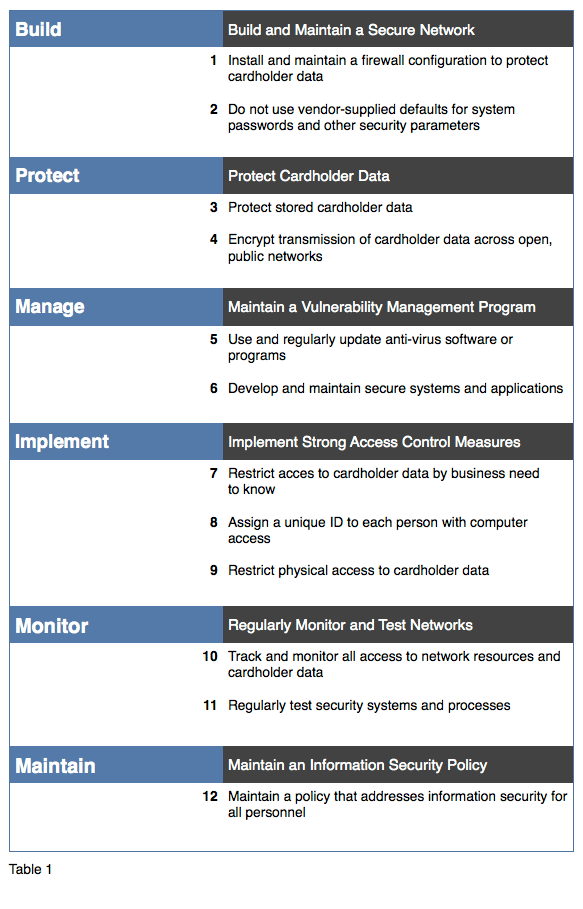
Compared to other regulatory or legislative standards, PCI's Data Security Standards (DSS) remains one of the least challenging for IBM i security officers to interpret. It does, however, still require resources to remediate. Most of the requirements are well-served by commercial security applications. For example, Requirement 1 can be addressed by implementing a transactional firewall, such as PowerTech Network Security, and Requirement 5 can be satisfied by deploying StandGuard Anti-Virus from Bytware. But there's no "silver bullet" to achieving PCI compliance, and most requirements involve utilization of IBM i's integrated security controls.
Admittedly, PCI DSS is far from perfect. It often relies on "self certification" that systems and practices truly are (and remain) compliant. This is prone to abuse and misunderstanding. In fact, the recent data breach at Global Payments of 1.5 million credit card numbers has brought about speculation that the company wasn't PCI-compliant. Not surprisingly, they've been dropped by Visa from the list of PCI-compliant companies. Regardless, compliance is not a guarantee that a server isn't vulnerable to attack. If PCI DSS is taken too literally, there's the potential that organizations will be lulled into a false sense of security. PCI is not the be-all and end-all of security. Rather, it outlines a set of base requirements that a company should meet in order to have any chance of protecting critical data.
Despite its obvious shortcomings, I'd offer that all companies should consider adhering to the PCI DSS directive as part of their best security practices. In fact, if you replace "cardholder data" with "application data" in the table above, you get a mandate that helps direct the protection of all organizations, regardless of the type of data they store. Far too often, companies do the minimum necessary, as it supposedly costs less and takes less effort. As Global Payments is now finding out—and they are certainly not alone—the reality can prove to be far different in the long run.
Unfortunately, many of the firms certified to conduct PCI audits remain unfamiliar with IBM i and its uniquely integrated database and security controls. As a result, recommendations often make no sense to those who have experience working with the platform. This lack of familiarity also increases the risk that data will be compromised, as there's a very real likelihood that serious configuration vulnerabilities will be missed.
PowerTech, a leading security and compliance company, has published a white paper discussing how PCI DSS requirements impact servers running IBM i. The document includes ways that PowerTech's comprehensive suite of security solutions can assist in achieving and maintaining PCI compliance. If your organization stores or processes data subject to regulation—such as credit card numbers—then this document is a must-read resource.
For more information on PowerTech's comprehensive suite of security solutions for achieving and maintaining PCI compliance on IBM i, visit www.powertech.com.












 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online