When first learning how to use Wireshark, it can be overwhelming. This TechTip has us dissecting a single frame.
Editor's note: This article is a follow-on to TechTip: Get Familiar with Wireshark, an Open-Source Packet Analysis Tool.
I have spent years immersing myself in packet analysis, and to help you get started, we will examine one single frame in Wireshark. In this example, I have opened a pre-captured trace file shown in Figure 1, where I have requested a webpage. The conversation is between the two endpoints 23.15.7.155 and 192.168.1.102.
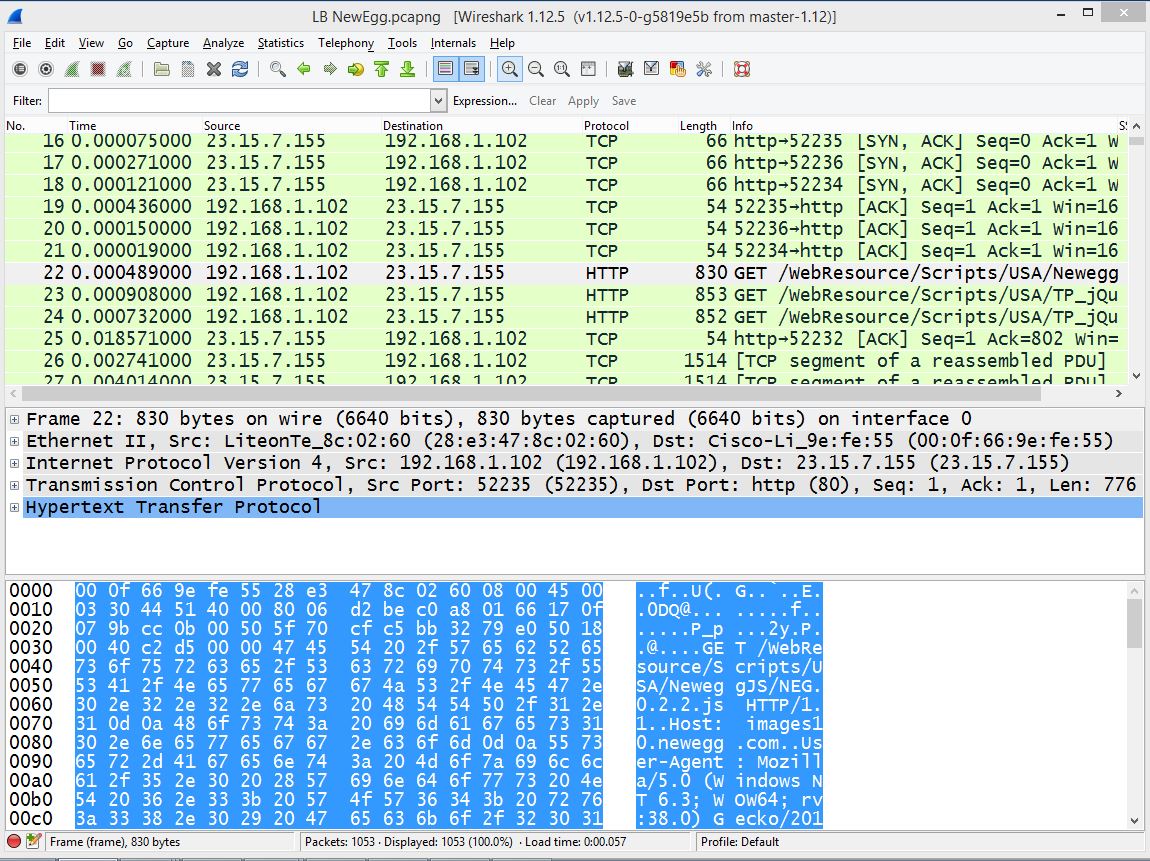
Figure 1: Here's an example of a pre-captured trace file.
You can start by going to View, and unselecting Packet List and Packet Bytes, which will give you more room on your screen. I will then expand the headers for Frame 22.
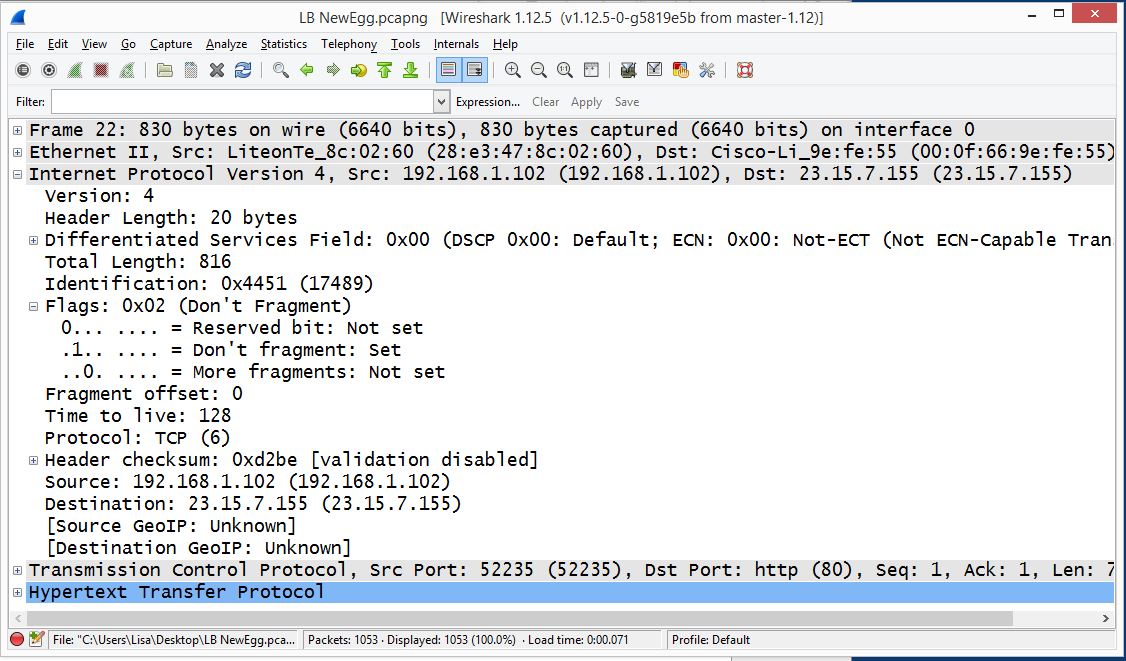
Figure 2: Here's the first part of Frame 22.
I have selected an HTTP frame, so in Figure 2 there will be the three headers (Frame header, IP Header, Transport Layer Header) and then the HTTP Header.
On the top of the pane, you will see the Label Frame 22, which is created by Wireshark to provide metadata about that single frame.
We then see the true headers, which includes the frame header, "Ethernet II", IP header, TCP header followed by the HTTP Header.
The Ethernet II Frame Header holds the values of the source and destination MAC addresses. To see the structure of an Ethernet Header visit https://wiki.wireshark.org/Ethernet .
Next is the IP Header. Underneath the header, we see its Version 4. The header length states 20 bytes, which is normal. Differentiated services, or DiffServ, indicates the quality of service for this data stream. In this case, it's set at zero (default), which is simply best-effort. The total length is the IP Header and any data that follows the header.
The Identification Field indicates the ID field of this packet. The ID field was used to keep track of fragmented packets, where all fragmented packets would have the same ID. In today's networks, we don't fragment data, so each packet should have a unique ID.
The flags are specifically used for fragmentation. This first flag is the reserved bit; it is not used. The second flag is Don't Fragment. And the third flag is More Fragments. In most, if not all, cases, you should see the Don't Fragment flag set. The Fragment Offset would be used if we did fragment.
The time to live is how many times it can hop through different routers before it times out and is dropped. Often, the default value is 64 or 128. The protocol field indicates what header follows the IP header, and in this case, you see its TCP.
In an IP Version 4 header, there's also header checksum, used for error detection, not correction, on a network. I point this out because in IPv6 there is no checksum. And then you see the Source IP address 192.168.1.102 and Destination IP address 23.15.7.155.
One other thing that you'll see in Wireshark is GeoIP. This reference is the GeoIP databases that can be used in conjunction with Wireshark to show exactly where packets were sent and where they were received.
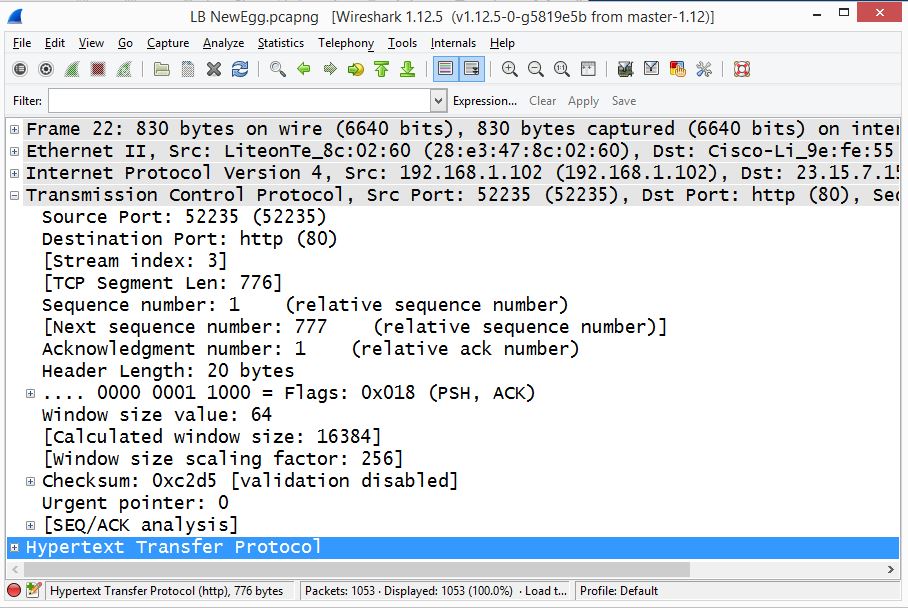
Figure 3: Frame 22 now has the TCP Header expanded.
The TCP header as shown in Figure 3 has some significant fields. The source port is 52235, which is sent by the client saying, "When you return data, send it to this port." The destination port is 80, which would make sense, because this is an HTTP connection.
The next line you see is "Stream index: 3". There is no stream index field in a TCP header. This is another way Wireshark helps you keep track of the data. A stream is an IP address and a port address, which represents a socket. Of course, when you have a large capture, you'll see many streams.
The sequence number is used to keep track of how much data has been sent. The Acknowledgement number informs the sending host that the data was received successfully. Relative sequence and acknowledgement numbers are used in Wireshark so you can see a smaller number rather than the actual (larger) number; however, you can turn off this option.
The header length states 20 bytes, which is normal. Then you will see the flags. In a TCP Header, there are eight flags, which tell the story of what is happening in the current transaction. The PSH and ACK flags are set here. Push indicates "don't wait for any more packets; send the data straight to the receiving socket."
The Window Size is a value set to notify the host how much room is available in the buffer. Modern devices have a larger buffer, so a scaling factor is used to give the true value of the receive window size. There's also header checksum, used for error detection.
That should give you a start in diving deeper into packet analysis. For some fun downloads, check out https://wiki.wireshark.org/SampleCaptures or http://packetlife.net/captures/ .












 IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
LATEST COMMENTS
MC Press Online