Accessing Linux and Windows systems can be as simple as using two open-source tools, SSH and VNC.
Much of my work for my employer is done at home after normal work hours, when I can access systems much faster because users are not logging on and off of the network. So how do you go about accessing your systems securely?
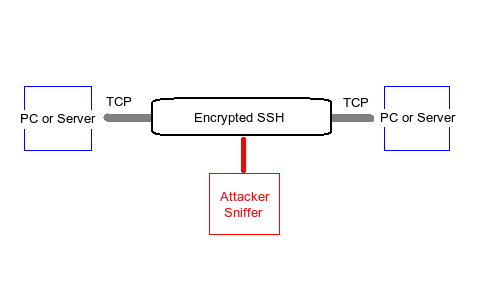
The answer to this can be anything from using a full-blown VPN to something as simple as tunneling and port forwarding across SSH (Secure Shell) and VNC (Virtual Network Computing). Tunneling and port forwarding is a means to send otherwise unsecured and unencrypted TCP packets across two points using an encrypted SSH channel. Some people refer to this as the poor man's VPN. My poor man's drawing below shows an example of how this traffic is visualized.
Figure 1: This basic diagram shows how SSH "tunnels" or encrypts data across a connection.
SSH Tips
Before I start explaining the tools and software available, I would like to make a note about the many differences between firewalls encountered. You might need to tweak any firewalls you have sitting on your network to allow using the ports SSH and VNC require for use. If you're not in charge of this, make sure you talk to your network administrators to help you set up the access needed or to further your knowledge on how your network operates. Every network is a little bit different in policy and use. Port 22 is the default SSH port and is commonly sniffed, so you might want to use a different port to help secure yourself from common attacks.
For instance, at my home, I have a firewall allowing inbound port 22 SSH access to only a specific machine. I then lock down SSH by using key authentication, which ensures that only the machines I have keys on can connect to my home network. Other methods include using utilities to watch these ports (for example, see the TechTip about securing SSH that I wrote). Search the Internet to find the solution that works best for your particular situation.
TightVNC Server
As mentioned, the two basic tools you'll need are SSH and VNC. On Linux machines, OpenSSH is already part of virtually all installations, and it can be used on the command line easily enough. I prefer using Tight VNC on Windows machines, but you can find replacements if you choose to use another client. In this example, I'll use a Linux laptop running CentOS 5.1 accessing a Windows XP box at work by port forwarding VNC's default port of 5900 to the local Linux laptop. This will be encrypted through SSH.
The first thing to do is to install TightVNC on the Windows PC. Installation is easy; GUI installer prompts explain every step. At the end of installation, make sure you set a password so that you have to authenticate to the PC before being able to connect to the display.
If you want to access Linux desktops instead of Windows across the remote connection, the same holds true for Linux. A VNC server must be configured on the Linux machine. The package you need to do so is called vncserver. A quick Google search will yield plenty of guides on setting up vncserver on a Linux box.
SSH Server
Next, you'll need an SSH server. The SSH server can reside on the same machine as the TightVNC server, the Windows machine, or a Linux server. I prefer the latter, because my SSH server at my employer serves as my gateway to the entire network from outside. Remember, you'll need to talk to your network administrator about inbound IPs and firewall rules regarding the setup.
Setting up SSH on Linux is a simple process. The packages on CentOS that provide these services are openssh and openssh-server. They should already be installed, but in case not, follow along below. Navigate to the configuration directory after installation and set a few parameters. You can change the port in this configuration if you'd like.
# yum install openssh openssh-server
# cd /etc/ssh
# vim sshd_config
port 22 -> Change to a different port if you'd like
Protocol 2
PasswordAuthentication no -> Change to no after you set up keys
ChallengeResponseAuthentication no
PermitEmptyPasswords no
X11Forwarding yes
# service sshd start
There are many options to set in here, but the important ones are listed above. Ensure that you only allow SSH protocol 2 because protocol 1 is extremely insecure. Using password authentication will have to be enabled at first until you decide to set up keys. When disabled, it will not allow any host to connect with a user account password; instead, it relies on the key system. There are a lot of resources and different ways to set this up. Do an Internet search for "ssh keys Linux" or "ssh keys," and you'll find many guides to help you understand SSH keys.
VNC Viewer
Now that you have SSH running on the server, you'll need to use the VNC viewer portion to connect to the TightVNC service running on the Windows PC. This package needs to be installed on the laptop.
# yum install vnc
The vncviewer can be accessed on the command line or through your menu system. You can configure settings such as encoding, color levels, inputs, and sharing. The settings that are configured by default work well.
The Remote Connection
Now that everything is set up, you can make a connection. Launch an SSH command to forward VNC's port 5900 to your local Linux laptop, passing through the SSH server setup on the host inside your company or home network. Again, this means you've already configured all firewalls to allow or forward this access. If you're using this to access a home network and you don't have DNS services, then substitute your name for actual IP addresses.
On the Linux laptop:
# ssh -L 5900:remote_windows_host:5900 user@inside_ssh_server
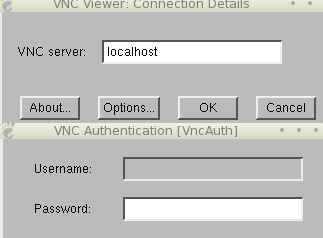
Launch the VNC viewer application and type localhost into the machine to connect to. Figure 2 shows you what the VNC viewer box should look like before and after you connect. Once connected to the VNC session, use the F8 key to open the VNC menu for options. You should now be connected to the Windows desktop.
Figure 2: Connect to port 5900 on localhost after forwarding across SSH.
Other Forwarding Tricks
Forwarding displays and GUIs are just one example of using this method for accessing remote networks. You can forward virtually any port you want. If you have internal Web applications that aren't accessible from the outside, you can easily port forward and tunnel this connection as well. I have a temperature monitor in my server room that I like to check on every now and again, but it's completely isolated inside. On the outside Linux laptop, launch the following command. Port 80 represents the port of the inside that you want to forward, and port 8080 represents the port on the local laptop.
# ssh -L 8080:remote_web_url:80 user@inside_ssh_server
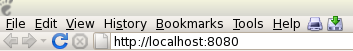
Next, open up a Web browser and type the following URL to access the local 8080 port that you just forwarded.
Figure 3: Port forward Web ports to localhost across Firefox.
Running SSH Servers and Clients on Windows
This TechTip has concentrated on using SSH server and clients on Linux hosts, but don't fret, because you can also use SSH on Windows using several different open-source projects. The first is Cygwin, which is a Linux-like environment installed into Windows. The second utility, called PuTTY, is a lightweight Win32 SSH/Telnet client. Both of these tools allow you run SSH from Windows hosts.
The Power of SSH
As you can see, the combination of just two small projects and a few minutes of time can give you an avenue to access systems remotely. While this method is not as fully functional as a dedicated VPN solution, it does allow you to get your work done while traveling without the expense of costly software and, more importantly, by using a secure and simple method of packet transportation. Your traffic might be sniffed by malicious beings, but it will not be smelled.












 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online