Can anyone really predict the future?
This time of year brings holiday cheer--parties, days off, time with family, gift exchange. It also brings out the prognosticating pundits who want you to believe they know what will happen in 2009. News flash: they don't know. But in an age-old tradition, to meet the expectations of their audiences, they spout predictions anyhow. So go ahead, read them; we all do. Consider this though: when was the last time you saw an analysis of last year's predictions to see how these pundits fared? Answer: rarely if ever.
What we can do with some credibility, however, is point out some important issues to consider in 2009 for those in decision-making roles involving enterprise technologies. Not predictions per se, but current truths that will extend into 2009 and affect how enterprise technology gets done to effectively serve enterprise missions.
- The economic realities are the backdrop to everything.
- The cloud is where much computing moves, depending on attitudes more than cost/benefits.
- The vendor consolidation in 2009 should accelerate, creating a moving target for buyers.
- The green revolution continues as a cost-saving and ethics-driven initiative in many corporations.
- The smarter phone adds applications for business as well as security issues.
- The impatient executive seeks quick, accurate answers from technology, without the need to master something new.
- The social consumer is the social employee, driving social computing into the enterprise.
- The growth of open-source applications continues in the mid-market, primarily because of perceived cost-savings.
- The proper uses of technologies to improve security of personal data is long overdue.
- There will be more rigorous enforcement of regulations, greater attention to governance, and a resurgence of corporate responsibility.
The economic realities are the backdrop to everything (employment/careers, vendor negotiations, and outsourcing). Companies will surely fail, jobs will be lost, and money will be tight in many sectors, likely reducing overall growth in spending on technology. While the good news is there is still projected spending growth for technology, spending projections vary, and many analysts have reduced their technology spending optimism for 2009. Gartner Group, for example, projects IT budget growth in the range of 0 to 3.3 percent in 2009. Meanwhile, Forrester is projecting growth of 6.1 percent, down from earlier projections of 9.4 percent growth for the year. But there are upsides to all of this for small and midsize companies. Vendors should be more malleable in their negotiations, so companies need to push for concessions--not only lower prices but additional services and more-favorable contract terms. Outsourcing can continue to be a weapon for many companies if used smartly. Proper management of outsourced projects is a must to realize cost savings. Other labor initiatives can save money also, including telecommuting, temporary staffing, and partnerships with higher-education institutions.
Like many workers around the world, those in IT fear for their jobs in this uncertain economy. However, consider what my colleague Maria DeGiglio so eloquently asserts in her recent article "The Best of Times, The Worst of Times": "The worst of times for employees in other lines of business sometimes means it is the best for times for IT professionals. The mainstream media does not differentiate; it makes its bucks on broad-brush statements and hype, especially doom and gloom. While I'm not downplaying the economic crisis and its uncertain aftermath, IT professionals are likely in a safe place--for the time being. So it's time to reign in spending, start saving, think creatively and outside the box, and be prepared."
The cloud is where much computing moves, depending on attitudes more than cost/benefits.
SaaS will continue to grow in use in SMBs and elsewhere as more end users learn about its benefits and vendors deliver SaaS alternatives to their solutions. SaaS offers the ability to quickly implement applications without IT people. Plus lower initial costs often provide SMBs with an attractive alternative. However, SaaS has perceptions to overcome with regard to security and, in some cases, functionality and performance.
According to research from Saugatuck Technology, in most SMBs, technology acquisition is trial and error handled on an application-by-application basis. Suite selection is rare for anything other than office-style applications (word processing, spreadsheet, presentation). IT in many SMBs is considered a tactical business resource. As with all technologies, decision-makers need to weigh the pros and cons of SaaS with their requirements and communicate those to others in the business.
The vendor consolidation in 2009 should accelerate, creating a moving target for buyers. With valuation of many technology companies near all-time lows, consolidation seems inevitable with the bigger growing by gobbling up others. Companies may go out of business. Buyers should protect themselves from bad things that can happen through vendor mergers and acquisitions by having solid contracts addressing what happens should an acquisition or a bankruptcy occur. Where appropriate, for example, software escrow can provide protections.
The green revolution continues as a cost-saving and ethics-driven initiative in many corporations. While new in many places, being green is being taken very seriously in many organizations. Most green initiatives in organizations require information from a variety of sources, essentially a data warehousing exercise. In addition, the pressure is on to reduce power consumption in data centers and review technology disposal practices. Thus, equipment consolidation initiatives will continue. Whether SMBs will pay much attention to vendor power-savings or green claims in 2009 remains to be seen. SMBs are unlikely to make the green choices based solely on the eco-friendliness of a technology solution unless there are additional accompanying benefits to the businesses.
The smarter phones add applications for business as well as security issues. Information on the go is nothing new for businesses, but the smartphone platforms are relatively new, with Apple's iPhone, Google's Android, Microsoft's Windows Mobile, Nokia's Symbian, and RIM's BlackBerry leading the market mix. All promise communications improvements for business people, with integrated contact management, Internet access, document management, navigation, and more. However, for SMBs, lack of interoperability, high costs, and carrier lock-in prevent easy deployment. Meanwhile, security concerns affect IT's willingness to embrace any of the platforms. The typical enterprise will see a mix of smart phones and will experience limited additional business value from the newer smartphone features in 2009.
The impatient executive seeks quick, accurate answers from technology, without the need to master something new. Busy executives in 2009 will be concerned with getting information to make difficult decisions in the tough economic climate. Business Intelligence (BI) remains critical as organizations can only understand their status by combining data from multiple sources and rolling it up into easy-to-interpret reports and dashboards. Not only does technology being used by executives need to be simple to access, but also concepts around technologies requested for the business must be quickly digestible. The onus is on IT to communicate effectively how technology spending benefits cash-strapped businesses in 2009.
The social consumer is the social employee, driving social computing into the enterprise. So your CEO is unlikely to know what Twitter is, let alone use it. But chances are your marketing VP knows about it. Many professionals use online social networks such as LinkedIn and Facebook. People want to be connected, whether for personal or professional purposes. As more people jump into these networks, they will seek to somehow expand the benefits into their organizations. This could be through social computing technologies built for businesses, including virtual worlds. While IT is likely to resist the invasion of social computing within the firewall, it is inevitable and will continue to occur in SMBs in 2009.
The growth of open-source applications continues in the mid-market because of perceived cost-savings. Open source is considered for more than half of business software acquisitions, is widely used in SMBs, and is in the enterprise to stay. With the cost pressures sure to be looming in 2009, open source garners even more attention. However, the savings expected can be elusive, especially when all cost factors are accounted for in the evaluation. Proprietary solutions can offer stronger integration and technical support. As I wrote in my July article, "Open-Source Software: Evolving Toward Broader Acceptance," open source can be confusing for enterprises. It is important for businesses to evaluate open-source software the same ways they evaluate proprietary solutions. Also, they should understand the different licenses and their implications. Lastly, they need to understand the open-source communities to determine how to obtain fixes and support.
The proper uses of technologies to improve security of personal data is long overdue. The amount of personal data not properly protected by businesses and governments of all sizes is staggering and embarrassingly shameful. Many of the data breaches are not sophisticated hacks but relatively straightforward breaches into weakly protected environments.
The Open Security Foundation (OSF) has a DataLossDB (datalossdb.org) that gathers information about events involving the loss, theft, or exposure of personally identifiable information (PII). According to the OSF, so far in 2008, stolen laptops, hacks, and Web breaches together represent more than half of the security breaches (see Figure 1). Incidents involving Social Security numbers and names and/or addresses together comprise 70 percent of incidents in 2008. Three quarters of the breaches come from outside enterprises. Clearly, organizations need to improve their protection of PII.
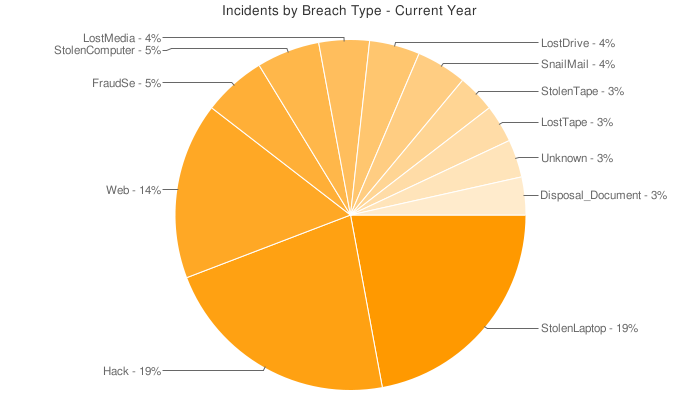
Source: Open Security Foundation
Figure 1: In 2008, stolen laptops, hacks, and Web breaches together represented more than half of the security breaches. (Click image to enlarge.)
There will be more rigorous enforcement of regulations, greater attention to governance, and a resurgence of corporate responsibility. Especially in the financial services sector, scrutiny of businesses will be at unprecedented levels in 2009. Whether true or not, the perceptions are that the collapses triggering economic shakiness are the results of lax regulations, inattention to governance, and corporate greed. With an incoming Obama administration in the U.S. promising to clean up the mess, businesses (especially those receiving or seeking government aid) will be held accountable. Technologies are central to governance and corporate responsibility and need to be honed to the new business realities.
Finally, there are some things most executives still won't understand in 2009, including service-oriented architecture (SOA), Web 2.0, virtualization, and unified communications. Why? Because there has been so much hype and so few real-world case studies on these things that people in SMBs either don't understand what they are or don't care. I know; there's a vocal community of consultants, bloggers, and vendor marketeers hovering around SOA, touting its ability to save IT from itself. Some businesses are using it, yet often not because they are selecting SOA but because they are selecting applications that happen to operate on SOA principles. So there is a bit of the tail-wagging-the-dog going on with SOA hype.
What is Web 2.0, and why should any SMB care? There is no standard definition, so we can say it's a mix of mashups and browser applications, with a dash of social computing. However, whether this translates into business benefits is questionable. Again, it is the wrong focus. SMBs should look for applications that help their businesses do more for lower cost. If the application happens to be Web 2.0, fine. Virtualization and unified communications suffer similar fates. While perhaps exciting to the technologists, they mean little until someone shows the business people why they should care.
2009 portends to be a challenging and interesting year for enterprise technologies in SMBs. While no one can completely accurately predict what will happen, it is safe to assert that there are unlikely to be any huge surprises in the technology world and that individual and corporate behaviors do not change overnight. With adjustments to the realities of business in the new year, there will be more of the same that we saw in 2008: a generally conservative approach toward new technologies, a healthy skepticism in response to extensive analyst/media/vendor hype, and an embracing of what works. The most important thing an SMB IT manager or executive can do is to pay attention. Know the business, track the vendors and technologies important to the organization, prepare to be proactive, be ready to be reactive as needed, and take the opportunities when presented.












 IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
LATEST COMMENTS
MC Press Online